安安大家好,目前會遇到頻繁的跳藍色視窗,然後就重新開機,之前可能久久一次,近期頻繁到三天一次,且每一次跳的錯誤描述都不盡相同,頻繁到有點心力交錯,請大家給點方向或建議,還能怎麼救這台電腦…
簡述目前遇過跳藍屏的情形:
用chrome看youtube影片→藍屏
用edge看youtube影片→藍屏
開visual studio 看影片想打code→藍屏
用chrome下載雲端的東西→藍屏
電腦設備如下:
CPU: Amd r5 3600
MB : gigabyte B450 AORUS M
RAM: KLEVV DDR4 8GB*4 3200
SSD: MP33 PRO M.2 PCIe 1TB
電供: FSP 黑爵士D 550W
顯卡: NVIDIA GeForce RTX 2070
系統: Windows 11 22H2
目前已經嘗試過的處置手段:
1. 更新顯卡驅動
2. 更新主機板bios
3. 更新主機板的audio_realtech…(不確定那是啥)
4. 清理mcu風扇及散熱片的灰塵(沒有換mcu的散熱膏)
5. 清理 顯卡風扇及散熱的灰塵
為了檢測到底是誰在搞我,我也有進行一些簡易的測試,
目前已經做過的測試:
1. QuickMemoryTestOK → 目標測記憶體 → pass
2. FurMark → 目標測GPU → pass
3. AIDA → 目標測CPU → pass
4. Windows內建 記憶體檢測工具 →目標測記憶體 → pass
下面附上藍屏人權圖:minidmp
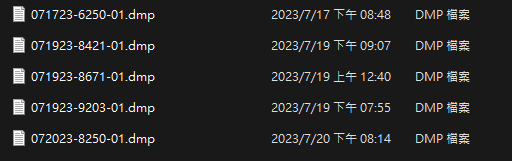
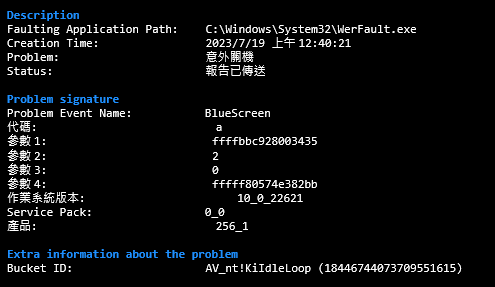
附上藍屏人權圖:事件紀錄








附上.dmp-1
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
IRQL_NOT_LESS_OR_EQUAL (a)
An attempt was made to access a pageable (or completely invalid) address at an
interrupt request level (IRQL) that is too high. This is usually
caused by drivers using improper addresses.
If a kernel debugger is available get the stack backtrace.
Arguments:
Arg1: 000000000002ff08, memory referenced
Arg2: 00000000000000ff, IRQL
Arg3: 000000000000002a, bitfield :
bit 0 : value 0 = read operation, 1 = write operation
bit 3 : value 0 = not an execute operation, 1 = execute operation (only on chips which support this level of status)
Arg4: fffff80523e6e3f8, address which referenced memory
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 2140
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 68900
Key : Analysis.Init.CPU.mSec
Value: 218
Key : Analysis.Init.Elapsed.mSec
Value: 15364
Key : Analysis.Memory.CommitPeak.Mb
Value: 94
Key : WER.OS.Branch
Value: ni_release_svc_prod3
Key : WER.OS.Timestamp
Value: 2023-06-22T09:51:00Z
Key : WER.OS.Version
Value: 10.0.22621.1928
FILE_IN_CAB: 072023-8250-01.dmp
BUGCHECK_CODE: a
BUGCHECK_P1: 2ff08
BUGCHECK_P2: ff
BUGCHECK_P3: 2a
BUGCHECK_P4: fffff80523e6e3f8
READ_ADDRESS: fffff8052491c468: Unable to get MiVisibleState
Unable to get NonPagedPoolStart
Unable to get NonPagedPoolEnd
Unable to get PagedPoolStart
Unable to get PagedPoolEnd
unable to get nt!MmSpecialPagesInUse
000000000002ff08
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXPNP: 1 (!blackboxpnp)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
TRAP_FRAME: fffff805232a3110 -- (.trap 0xfffff805232a3110)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=0000000000027104 rbx=0000000000000000 rcx=0000000000000001
rdx=0000000000000100 rsi=0000000000000000 rdi=0000000000000000
rip=fffff80523e6e3f8 rsp=fffff805232a32a0 rbp=0000000000000001
r8=8000000000000000 r9=0000000000000003 r10=0000fffff80523f6
r11=ffffa97be9400000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up di ng nz na pe nc
nt!KiSetClockTickRate+0x88:
fffff805`23e6e3f8 8983088e0000 mov dword ptr [rbx+8E08h],eax ds:00000000`00008e08=????????
Resetting default scope
STACK_TEXT:
fffff805`232a2fc8 fffff805`240442a9 : 00000000`0000000a 00000000`0002ff08 00000000`000000ff 00000000`0000002a : nt!KeBugCheckEx
fffff805`232a2fd0 fffff805`2403f934 : ffff9204`8883b000 fffff805`232a3210 ffff9204`88a0d000 00000000`00000000 : nt!KiBugCheckDispatch+0x69
fffff805`232a3110 fffff805`23e6e3f8 : 00000000`00000001 00000000`00027100 00000000`00000001 fffff805`22024f80 : nt!KiPageFault+0x474
fffff805`232a32a0 fffff805`23e73592 : 00000000`00000003 fffff805`2201c180 00000000`00027104 00000000`00027100 : nt!KiSetClockTickRate+0x88
fffff805`232a3300 fffff805`23e37aaf : fffff805`2201c180 ffffffff`ffffffff 00000000`00000000 fffff805`2201c180 : nt!KiSetNextClockTickDueTime+0x432
fffff805`232a34e0 fffff805`23e71e62 : fffff805`232a35a9 00000000`00000000 000000c1`bac12bcf 00000000`00000000 : nt!KiRestoreClockTickRate+0x77
fffff805`232a3530 fffff805`23e715b0 : 00000000`00989680 00000000`00000003 fffff805`2201c180 00000000`00989680 : nt!KeResumeClockTimerFromIdle+0x202
fffff805`232a3610 fffff805`23e709c1 : fffff805`2201c180 00000000`00000000 fffff805`232a3aa1 fffff805`232a3ab0 : nt!PpmIdleExecuteTransition+0x9c0
fffff805`232a3a50 fffff805`24033a34 : 00000000`00000000 fffff805`21cadb20 fffff805`2494c6c0 fffff805`2494c6c0 : nt!PoIdle+0x361
fffff805`232a3c40 00000000`00000000 : fffff805`232a4000 fffff805`2329e000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x54
SYMBOL_NAME: nt!KiSetClockTickRate+88
MODULE_NAME: nt
IMAGE_NAME: ntkrnlmp.exe
IMAGE_VERSION: 10.0.22621.1992
STACK_COMMAND: .cxr; .ecxr ; kb
BUCKET_ID_FUNC_OFFSET: 88
FAILURE_BUCKET_ID: AV_CODE_AV_nt!KiSetClockTickRate
OS_VERSION: 10.0.22621.1928
BUILDLAB_STR: ni_release_svc_prod3
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {bd948979-7836-a572-7a47-c56a592283ac}
附上.dmp-2
*******************************************************************************
* *
* Bugcheck Analysis *
* *
*******************************************************************************
ATTEMPTED_EXECUTE_OF_NOEXECUTE_MEMORY (fc)
An attempt was made to execute non-executable memory. The guilty driver
is on the stack trace (and is typically the current instruction pointer).
When possible, the guilty driver's name is printed on
the BugCheck screen and saved in KiBugCheckDriver.
Arguments:
Arg1: ffffae827e2f5a90, Virtual address for the attempted execute.
Arg2: 80000002889a6963, PTE contents.
Arg3: fffff8071b4e36c0, (reserved)
Arg4: 0000000000000000, (reserved)
Debugging Details:
------------------
KEY_VALUES_STRING: 1
Key : Analysis.CPU.mSec
Value: 2233
Key : Analysis.DebugAnalysisManager
Value: Create
Key : Analysis.Elapsed.mSec
Value: 150223
Key : Analysis.Init.CPU.mSec
Value: 671
Key : Analysis.Init.Elapsed.mSec
Value: 1141266
Key : Analysis.Memory.CommitPeak.Mb
Value: 95
Key : WER.OS.Branch
Value: ni_release_svc_prod3
Key : WER.OS.Timestamp
Value: 2023-06-22T09:51:00Z
Key : WER.OS.Version
Value: 10.0.22621.1928
FILE_IN_CAB: 071923-8421-01.dmp
BUGCHECK_CODE: fc
BUGCHECK_P1: ffffae827e2f5a90
BUGCHECK_P2: 80000002889a6963
BUGCHECK_P3: fffff8071b4e36c0
BUGCHECK_P4: 0
BLACKBOXBSD: 1 (!blackboxbsd)
BLACKBOXNTFS: 1 (!blackboxntfs)
BLACKBOXWINLOGON: 1
CUSTOMER_CRASH_COUNT: 1
PROCESS_NAME: System
TRAP_FRAME: fffff8071b4e36c0 -- (.trap 0xfffff8071b4e36c0)
NOTE: The trap frame does not contain all registers.
Some register values may be zeroed or incorrect.
rax=ffffae827e2f5a90 rbx=0000000000000000 rcx=ffffd40625bf8b00
rdx=ffffd40625bf8b48 rsi=0000000000000000 rdi=0000000000000000
rip=ffffae827e2f5a90 rsp=fffff8071b4e3858 rbp=fffff8071b4e3929
r8=00000000e404ce70 r9=0000000001d9ba41 r10=0000ffffae827e2f
r11=ffffb3f832800000 r12=0000000000000000 r13=0000000000000000
r14=0000000000000000 r15=0000000000000000
iopl=0 nv up ei pl nz na pe nc
ffffae82`7e2f5a90 20780a and byte ptr [rax+0Ah],bh ds:ffffae82`7e2f5a9a=fa
Resetting default scope
STACK_TEXT:
fffff807`1b4e3508 fffff807`1ee96b34 : 00000000`000000fc ffffae82`7e2f5a90 80000002`889a6963 fffff807`1b4e36c0 : nt!KeBugCheckEx
fffff807`1b4e3510 fffff807`1ee90877 : 00000000`00000011 00000000`00000003 00000000`00000000 fffff807`1b4e35e0 : nt!MiCheckSystemNxFault+0x24f8bc
fffff807`1b4e3550 fffff807`1ec7f82f : 80000002`889a6963 00000000`00000011 fffff807`1b4e3659 00000000`00000000 : nt!MiRaisedIrqlFault+0x258277
fffff807`1b4e35a0 fffff807`1ee3f829 : 00000000`00000000 00000000`00000000 00000000`00000000 00000000`00000000 : nt!MmAccessFault+0x3af
fffff807`1b4e36c0 ffffae82`7e2f5a90 : fffff807`1ed4b78b ffffd406`00000001 ffffd406`00000001 fffff807`00000000 : nt!KiPageFault+0x369
fffff807`1b4e3858 fffff807`1ed4b78b : ffffd406`00000001 ffffd406`00000001 fffff807`00000000 ffffd406`00000002 : 0xffffae82`7e2f5a90
fffff807`1b4e3860 fffff807`1ed492f4 : 00000000`00000000 00000000`00000000 00000000`00000000 fffff807`1a26a708 : nt!KiProcessExpiredTimerList+0x1eb
fffff807`1b4e3990 fffff807`1ee33a7e : 00000000`00000000 fffff807`1a264180 00000000`00000000 fffff807`1f74c6c0 : nt!KiRetireDpcList+0xa94
fffff807`1b4e3c40 00000000`00000000 : fffff807`1b4e4000 fffff807`1b4de000 00000000`00000000 00000000`00000000 : nt!KiIdleLoop+0x9e
SYMBOL_NAME: nt!MiCheckSystemNxFault+24f8bc
MODULE_NAME: nt
IMAGE_VERSION: 10.0.22621.1992
STACK_COMMAND: .cxr; .ecxr ; kb
IMAGE_NAME: ntkrnlmp.exe
BUCKET_ID_FUNC_OFFSET: 24f8bc
FAILURE_BUCKET_ID: 0xFC_nt!MiCheckSystemNxFault
OS_VERSION: 10.0.22621.1928
BUILDLAB_STR: ni_release_svc_prod3
OSPLATFORM_TYPE: x64
OSNAME: Windows 10
FAILURE_ID_HASH: {a6ae5288-6b71-974a-9b09-23f14d998164}