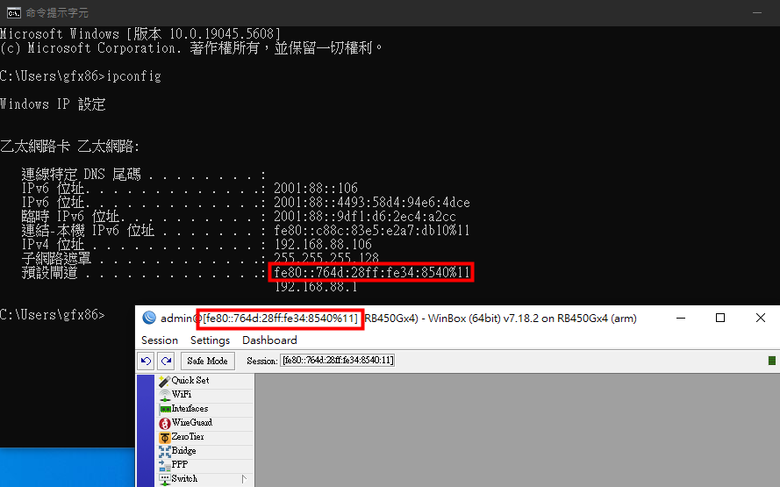
我是用RB450GX4,V6.49.18,有設定多撥 (撥7組PPPoE),
路由表裡面設定固定IP那組為default route,其餘的則是個別設Routing Mark,
並且將in-interface為固定IP撥號的pppoe client開啟fast track,
這時只有流入的流量(下載)的流量會套用fast track,
但是流出的流量(上傳)卻完全沒有fast track,
導致下載可以跑滿500M (CPU使用率也不高),
但是上傳到300多M就因為CPU瓶頸而上不去了
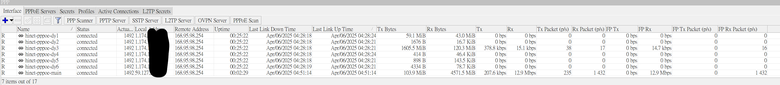
請問問題可能會出現在哪裡?
升級到v7後,因為支援WireGuard了,也想來試著用用看WireGuard
在main route table下,WireGuard運作一切正常,沒遇到什麼問題,
但如果在其他routing table下,就會發生無法連線的問題
Routing Table預設是main,走的是hinet-pppoe-main,我是想讓Wireguard的input走hinet-pppoe-dy5 interface, 已經有開啟Filter Rules的input了
Filter Rules
9 ;;; allow VPN (L2TP over IPsec)
chain=input action=accept protocol=udp dst-address-list=hinet-main dst-port=500,4500,1701 log=no log-prefix=""
10 chain=input action=accept protocol=ipsec-esp dst-address-list=hinet-main log=no log-prefix=""
11 ;;; allow VPN (L2TP over IPsec)
chain=input action=accept protocol=udp dst-address-list=hinet-dy5 dst-port=500,4500,1701 log=no log-prefix=""
12 chain=input action=accept protocol=ipsec-esp dst-address-list=hinet-dy5 log=no log-prefix=""
13 ;;; allow VPN (Wireguard)
chain=input action=accept protocol=udp dst-address-list=hinet-dy5 dst-port=53231 log=yes log-prefix=""
14 ;;; allow VPN (Wireguard)
chain=input action=accept protocol=udp dst-address-list=hinet-main dst-port=53231 log=no log-prefix=""
Mangle
27 ;;; vpn connection traffic from hinet-dy5
chain=prerouting action=mark-connection new-connection-mark=dy5-conn passthrough=yes in-interface=hinet-pppoe-dy5 log=yes log-prefix=""
28 chain=output action=mark-routing new-routing-mark=to-dy5 passthrough=yes connection-mark=dy5-conn log=yes log-prefix=""
29 chain=prerouting action=mark-routing new-routing-mark=to-dy5 passthrough=no src-address-list=internal-ip connection-mark=dy5-conn log=no log-prefix=""
30 chain=prerouting action=mark-routing new-routing-mark=to-dy5 passthrough=yes src-address-list=dy5-device dst-address-list=!internal-ip log=no log-prefix=""
有抓了一下封包,雖然Mangle規則可以把進到hinet-pppoe-dy5的連線做mark connection,
但是卻沒辦法對output的封包做mark routing,導致回傳的封包還是走hinet-pppoe-main
但同樣的規則,L2TP over IPsec卻可以正常從hinet-pppoe-dy5連入連線
不知道這是WireGuard本身的連線限制嗎?
自問自答
看來是老問題了
https://forum.mikrotik.com/viewtopic.php?t=210232
y2hxp wrote:in-interface是流量的來源接口,out-interface是流量的目的接口。
最近剛接觸mikrotik...(恕刪)
若是下載,就是 網際網路接口-> 區域網路接口;
反之上載,則是 區域網路接口-> 網際網路接口。
所以若要阻止某個https(443)網站(123.123.123.123)送封包進入您的家用網路(bridge1),可設置:
action=drop chain=forward in-interface=4g src-address=123.123.123.123 out-interface=brdige1 protocol=tcp src-port=443
因網站(123.123.123.123)是明確的ip,所以不強調網際網路接口(4g)也沒問題。
action=drop chain=forward src-address=123.123.123.123 out-interface=brdige1 protocol=tcp src-port=443
若只是想阻止網站(123.123.123.123)送封包至家中的pc(192.168.88.1),可設置:
action=drop chain=forward in-interface=4g src-address=123.123.123.123 out-interface=brdige1 dst-address=192.168.88.100 protocol=tcp src-port=443
因pc(192.168.88.100)是明確的ip,所以不強調家用網路接口(bridge1)也沒問題。
action=drop chain=forward in-interface=4g src-address=123.123.123.123 dst-address=192.168.88.100 protocol=tcp src-port=443
因網站(123.123.123.123)是明確的ip,所以不強調網際網路接口(4g)也不會有問題。
action=drop chain=forward src-address=123.123.123.123 dst-address=192.168.88.100 protocol=tcp src-port=443
———————————————————————————————————————
以上是下載(網站答覆)的情況,若是上載(向網站要求)的情況:
若要阻止家用網路(bridge1)向某個https(443)網站(123.123.123.123)要求連線,可設置:
action=drop chain=forward in-interface=bridge1 out-interface=4g dst-address=123.123.123.123 protocol=tcp dst-port=443
因網站(123.123.123.123)是明確的ip,所以不強調網際網路接口(4g)也沒問題。
action=drop chain=forward in-interface=bridge1 dst-address=123.123.123.123 protocol=tcp src-port=443
若只是想阻止家中pc(192.168.88.100)向網站(123.123.123.123)要求連線,可設置:
action=drop chain=forward in-interface=bridge1 src-address=192.168.88.100 out-interface=4g dst-address=123.123.123.123 protocol=tcp dst-port=443
因網站(123.123.123.123)是明確的ip,所以不強調網際網路接口(4g)也沒問題。
action=drop chain=forward in-interface=bridge1 src-address=192.168.88.100 dst-address=123.123.123.123 protocol=tcp dst-port=443
因pc(192.168.88.100)是明確的ip,所以不強調家用網路接口(bridge1)也不會有問題。
action=drop chain=forward src-address=192.168.88.100 dst-address=123.123.123.123 protocol=tcp dst-port=443
內文搜尋
X